pfSense
This tutorial explains how to set up a policy-based or route-based IPsec VPN with a pfSense device.
(Policy-based only) LAN interface configuration
- From the pfSense WebGUI, select Interfaces > LAN.
- Choose an interface from the Available network ports list.
- Select Add. The General Configuration dialog displays.
Refer to the image below for guidance on which values to use.
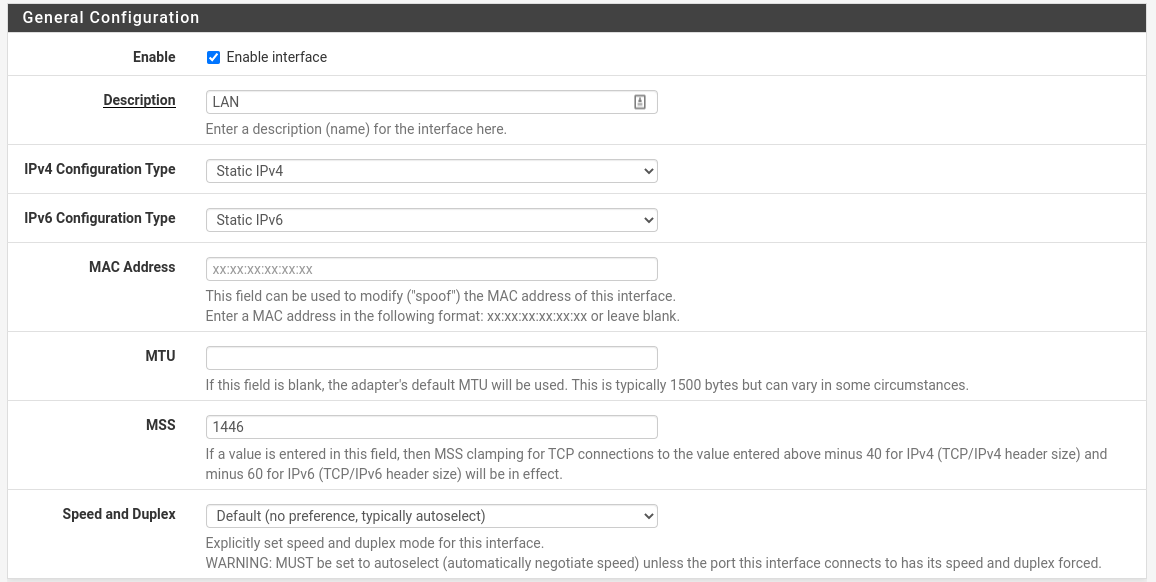
| Field | Value |
|---|---|
| Enable | ✔️ Enable interface |
| Description | LAN |
| IPv4 Configuration Type | Static IPv4 |
| IPv6 Configuration Type | Static IPv6 |
| MSS | 1446 |
Phase 1
Policy-based configuration
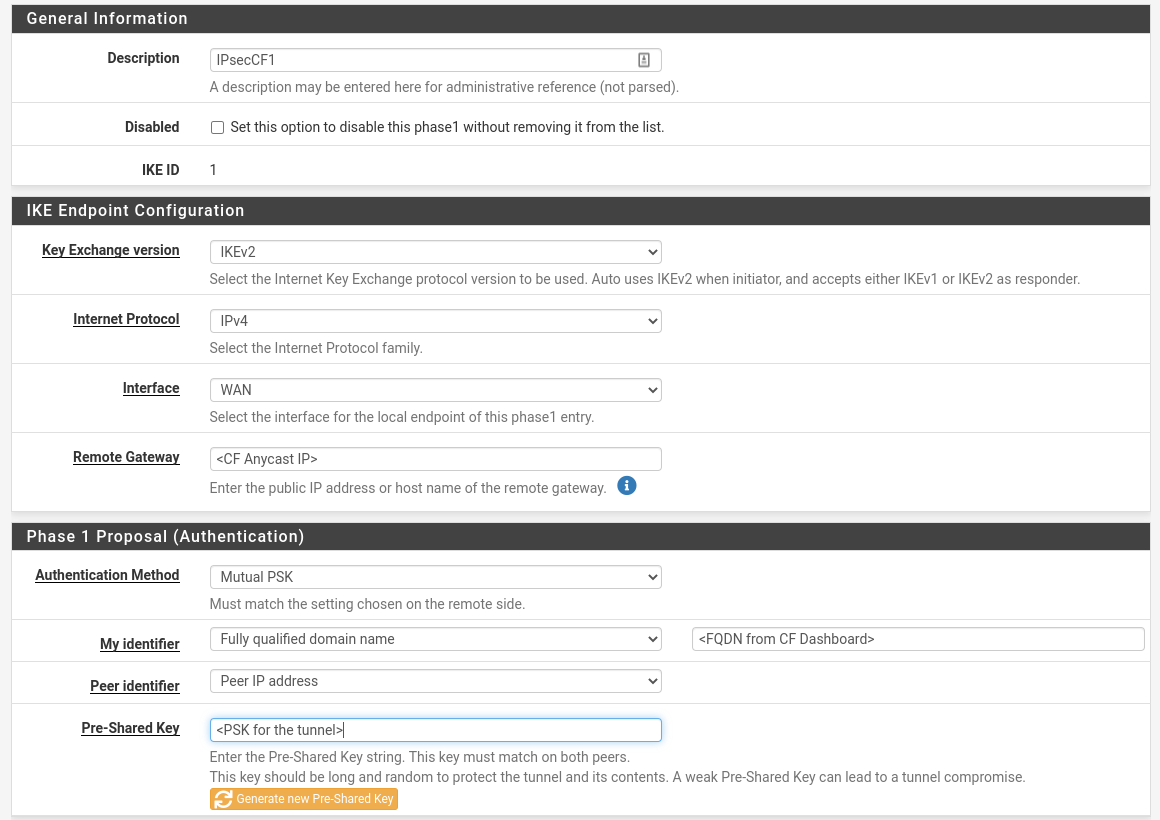
| Field | Value |
|---|---|
| Description | Name |
| Key Exchange Version | IKE v2 |
| Internet Protocol | IPv4 |
| Interface | WAN |
| Remote Gateway | <Anycast IP provided by Cloudflare> |
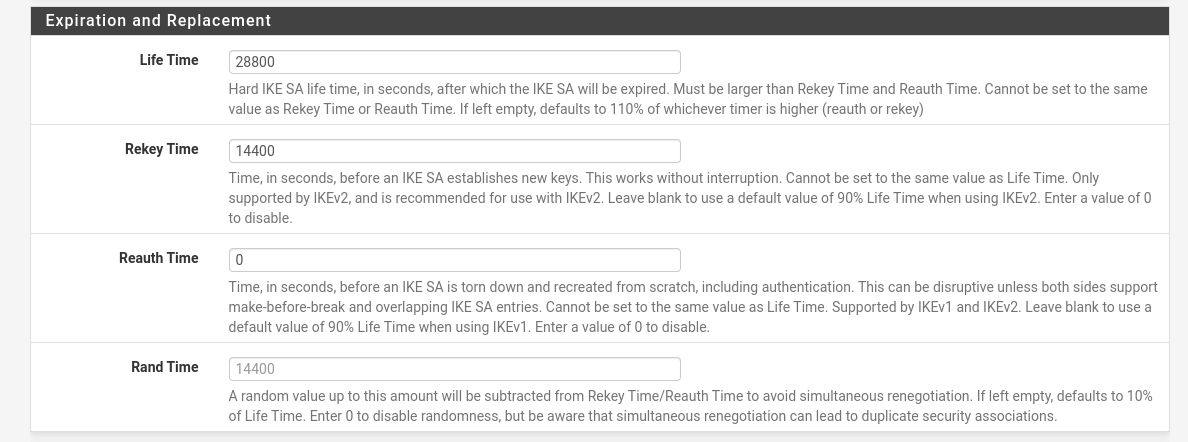
| Field | Value |
|---|---|
| Life Time | 28800 |
| Rekey Time | 14400 |
| Reauth Time | 0 |
Route-based configuration

| Field | Value |
|---|---|
| Description | Name |
| Key Exchange Version | IKE v2 |
| Internet Protocol | IPv4 |
| Interface | WAN |
| Remote Gateway | <Anycast IP provided by Cloudflare> |

| Field | Value |
|---|---|
| Life Time | 28800 |
| Rekey Time | 14400 |
| Reauth Time | 0 |
Phase 2
Policy-based configuration
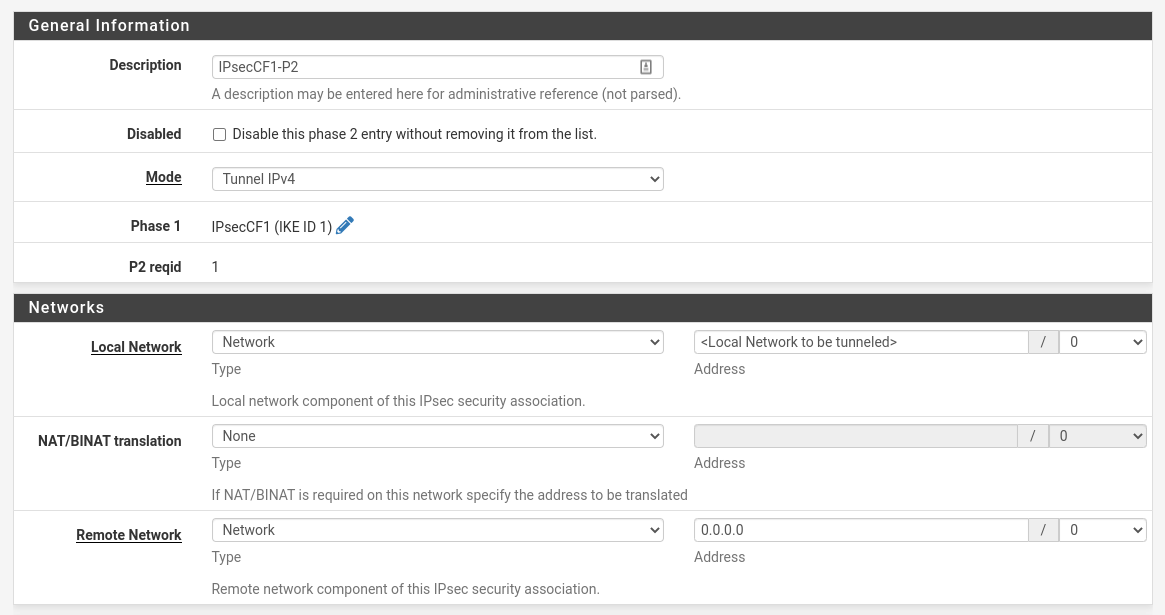
| Field | Value |
|---|---|
| Description | Name |
| Mode | Tunnel IPv4 |
| Local Network | <Local Network to be tunneled> |
| NAT/BINAT translation | None |
| Remote Network | Remote network available via the tunnel |
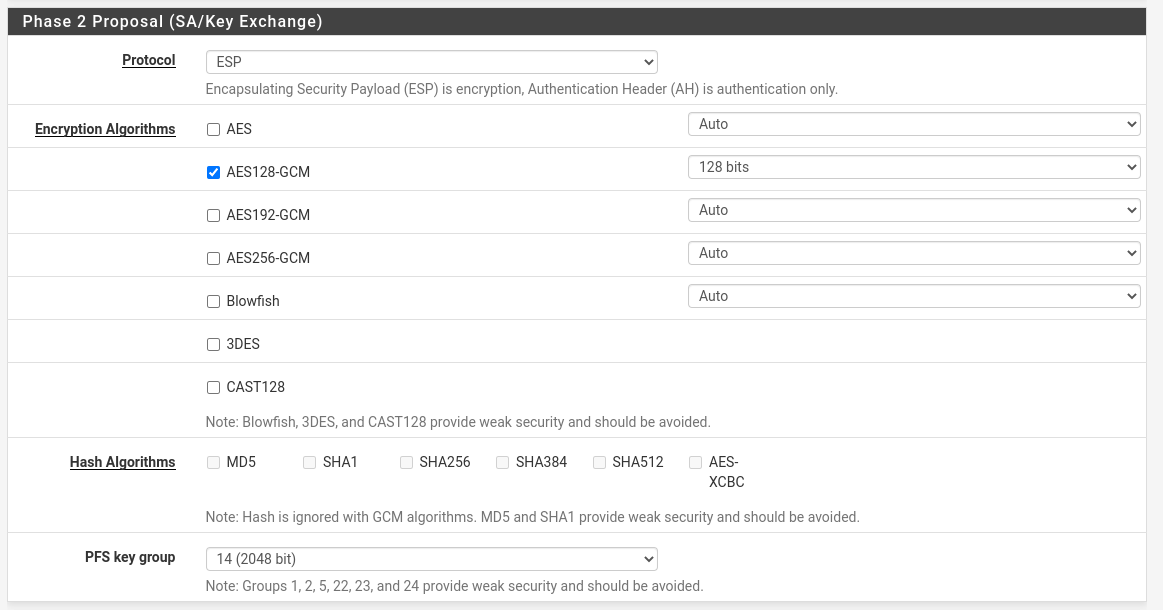
| Field | Value |
|---|---|
| Protocol | ESP |
| Encryption Algorithm | ✔️ AES128-GCM, 128 bits |
| PFS key group | 14 (2048 bit) |
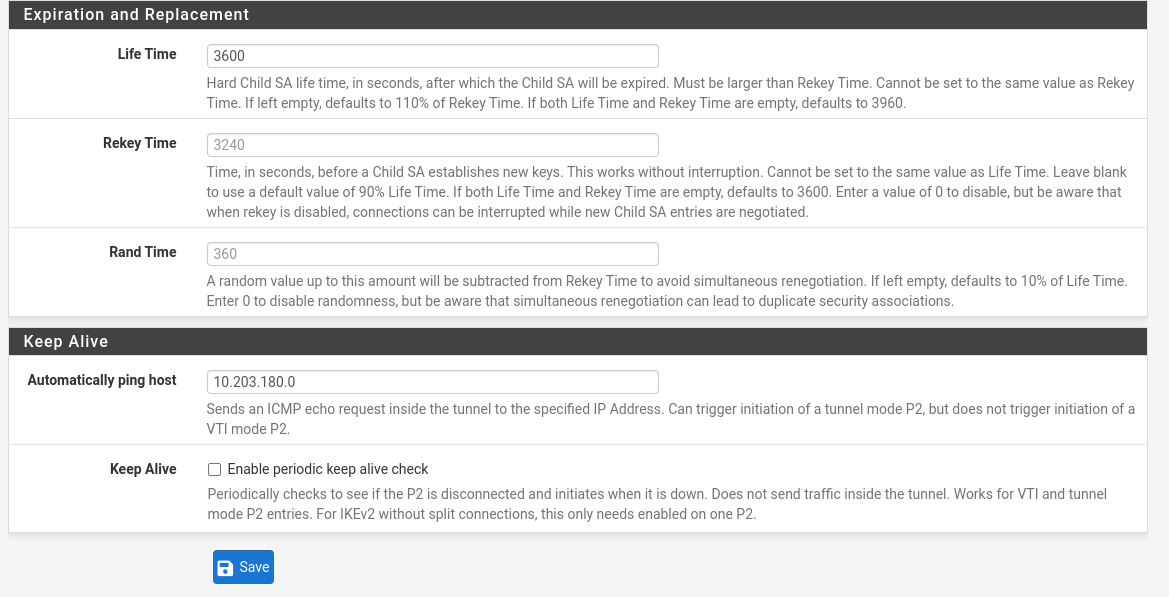
| Field | Value |
|---|---|
| Life Time | 3600 |
| Rekey Time | 3240 |
| Rand Time | 360 |
| Automatically ping host | Specify an IP address available via the tunnel. Refer to the Description field for more information. |
Route-based configuration
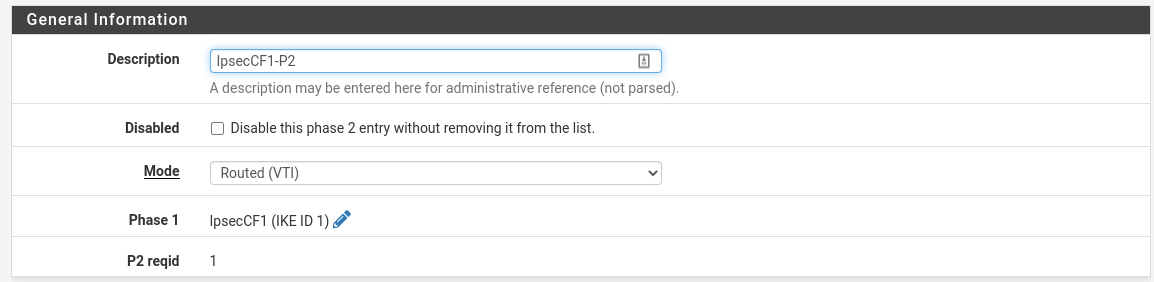
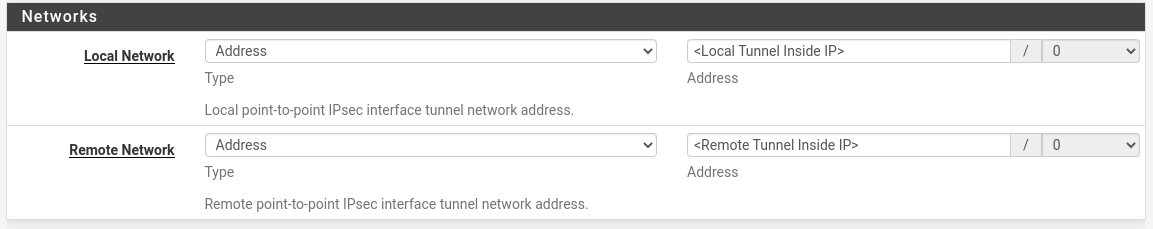
| Field | Value |
|---|---|
| Description | Name |
| Mode | Routed (VTI) |
| Local Network | <Local Tunnel Inside IP> |
| Remote Network | <Remote Tunnel Inside IP> |

| Field | Value |
|---|---|
| Protocol | ESP |
| Encryption Algorithm | ✔️ AES128-GCM, 128 bits |
| PFS key group | 14 (2048 bit) |

| Field | Value |
|---|---|
| Life Time | 3600 |
| Rekey Time | 3240 |
| Rand Time | 360 |
| Automatically ping host | Specify an IP address available via the tunnel. Refer to the Description field for more information. |
(Route-based only) Interface assignment
- From the pfSense WebGUI, select Interfaces > LAN.
- Choose an interface from the Available network ports list.
- Select Add. The General Configuration dialog displays.
Refer to the image below for guidance on which values to use.

| Field | Value |
|---|---|
| Enable | ✔️ Enable interface |
| Description | LAN |
| IPv4 Configuration Type | Static IPv4 |
| IPv6 Configuration Type | Static IPv6 |
| MSS | 1446 |
- From the pfSense WebGUI, select Interfaces > Assignments.
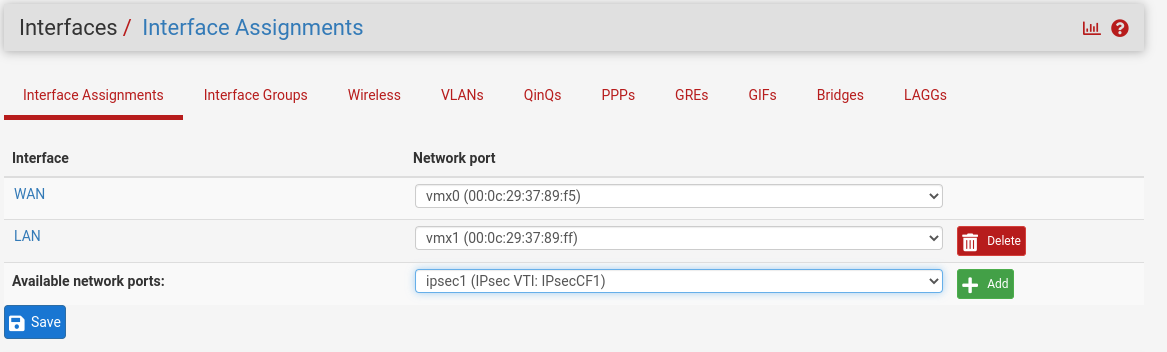
- From Available network ports, select + Add.
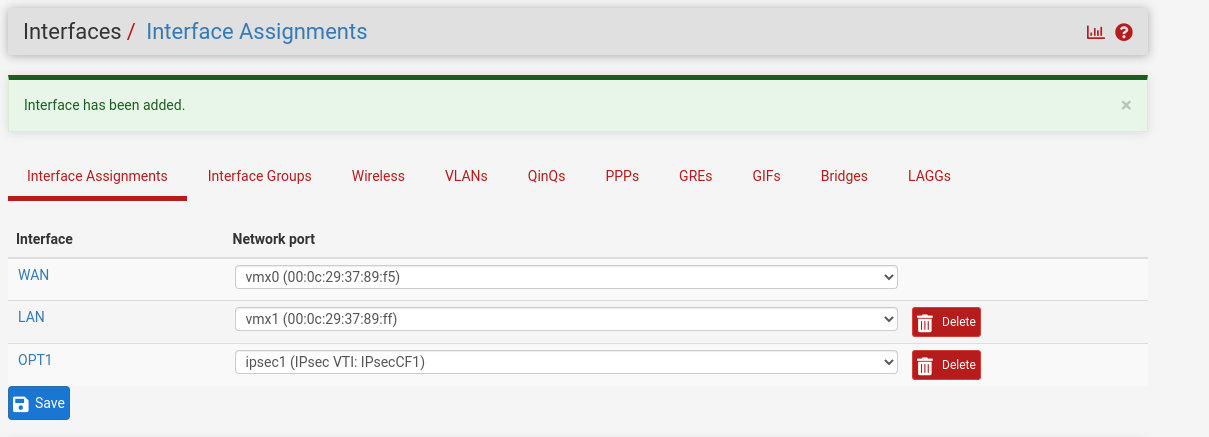
- Under Interface, select OPT1.
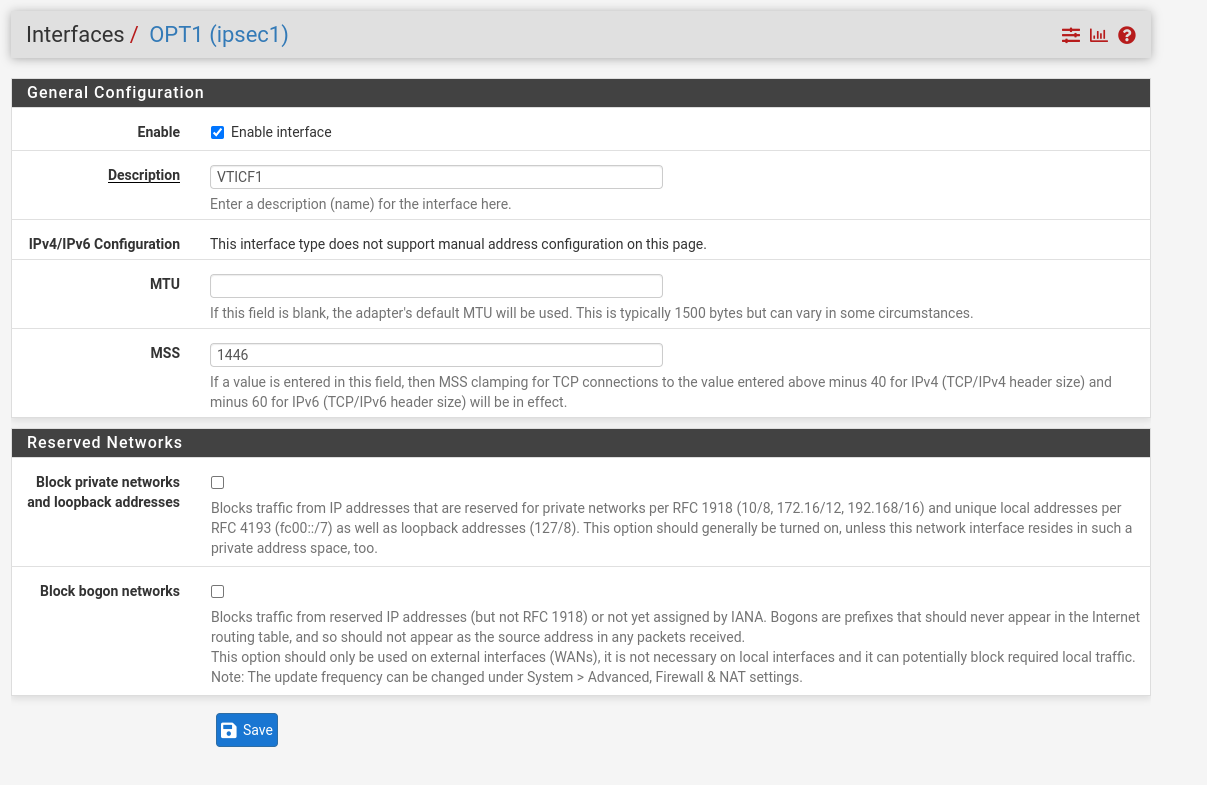
- Ensure Enable interface is selected.
- For Description, add a description to help you identify the interface.
- For MSS, enter 1446, which should be the same as the LAN interface.
- Select Save to save your changes when you are done.
Routing configuration
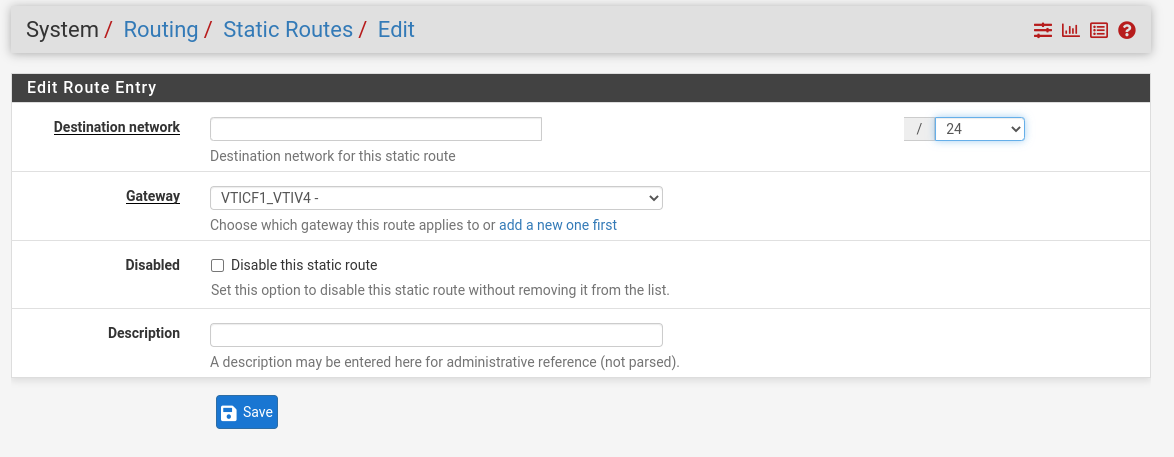
- From the pfSense WebGUI, select System, Routing, Static Routes.
- On the Static Routes page, select Add.
- Create static routes for all network that will be routed via the tunnel with Gateway as the IPsec VTI interface.
Firewall configuration
- From the pfSense WebGUI, select Firewall Rules.
- Select LAN.
- Ensure a rule exists that allows traffic from LAN to IPsec.
- Select Save when you are done.
If you need to allow traffic from IPsec to LAN, you will need to create rules that allow this.