Proxy DNS records
2 min read
The first - and often easiest - step of DDoS protection is making sure your DNS records are proxied through Cloudflare.
How it works
Without Cloudflare
Without Cloudflare, DNS lookups for your application’s URL return the IP address of your origin server.
| URL | Returned IP address |
|---|---|
example.com | 192.0.2.1 |
When using Cloudflare with unproxied DNS records, DNS lookups for unproxied domains or subdomains also return your origin’s IP address.
Another way of thinking about this concept is that visitors directly connect with your origin server.
With Cloudflare
With Cloudflare — meaning your domain or subdomain is using proxied DNS records — DNS lookups for your application’s URL will resolve to Cloudflare Anycast IPs instead of their original DNS target.
| URL | Returned IP address |
|---|---|
example.com | 104.16.77.250 |
This means that all requests intended for proxied hostnames will go to Cloudflare first and then be forwarded to your origin server.
How it helps
DDoS protection
When your traffic is proxied through Cloudflare, Cloudflare can automatically stop DDoS attacks from ever reaching your application (and your origin server).
Caching
Proxied traffic also benefits from the default optimizations of the Cloudflare cache. Cloudflare caches certain types of resources automatically, which both speeds up your application’s performance and reduces the overall number of requests.
Hides origin IP address
Proxying your DNS records in Cloudflare also hides the IP address of your origin server (because requests to your application resolve to Cloudflare Anycast IP addresses instead).
This obscurity makes it harder for someone to connect directly to your origin, which - by extension - also makes it harder to target your origin with a DDoS attack.
How to do it
Before proxying your records, you should likely allow Cloudflare IP addresses at your origin to prevent requests from being blocked.
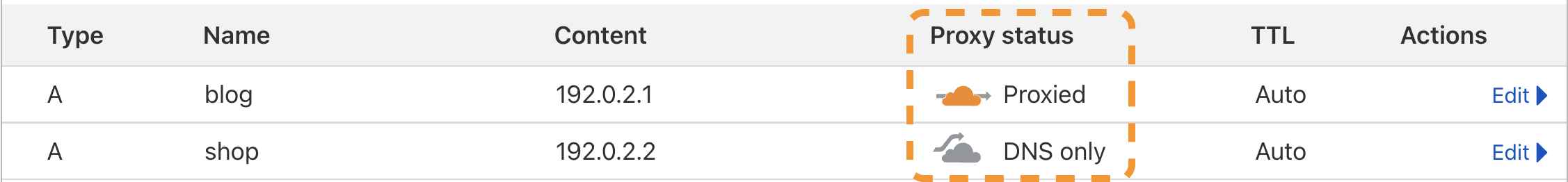
Then, update your Cloudflare DNS records so their Proxy status is Proxied.
Unit 1 of 4