Use Azure AD Conditional Access policies in Cloudflare Access
With Azure Active Directory (AD)’s Conditional Access, administrators can enforce policies on applications and users directly in Azure AD. Conditional Access has a set of checks that are specialized to Windows and are often preferred by organizations with Windows power users.
Prerequisites
- Global admin rights to an Azure AD account
- Configured users in the Azure AD account
1. Set up an identity provider for your application
Refer to our IdP setup instructions for Azure AD.
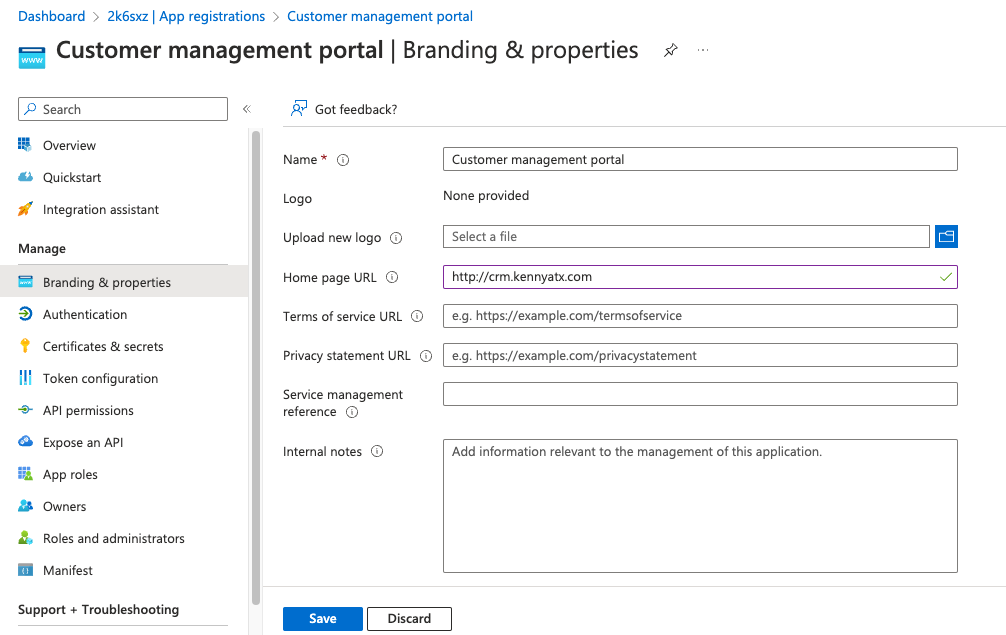
We suggest naming the IdP integration after the target application, for example Azure AD - Customer management portal.
2. Configure Conditional Access in Azure AD
In Azure Active Directory, go to App registrations and select the application you created for the IdP integration.
Go to Branding & properties.
In Home page URL, enter the hostname of the protected application.
Return to the Azure Active Directory dashboard and go to Enterprise applications.
Select your application.
Select Properties.
To show the application in the Microsoft App Launcher, change Visible to users to Yes. The application will appear when the user goes to My Apps.
Next, navigate to Conditional Access and build a new policy.
Create and enable any additional policies for your application.
3. Create an Access application
To enforce your Conditional Access policies on a Cloudflare Access application:
In Zero Trust, go to Access > Applications.
Create a new self-hosted application.
In Application domain, enter the target URL of the protected application.
For Identity providers, select only the IdP integration that was configured for this application. This limits which IdPs are shown to the user.
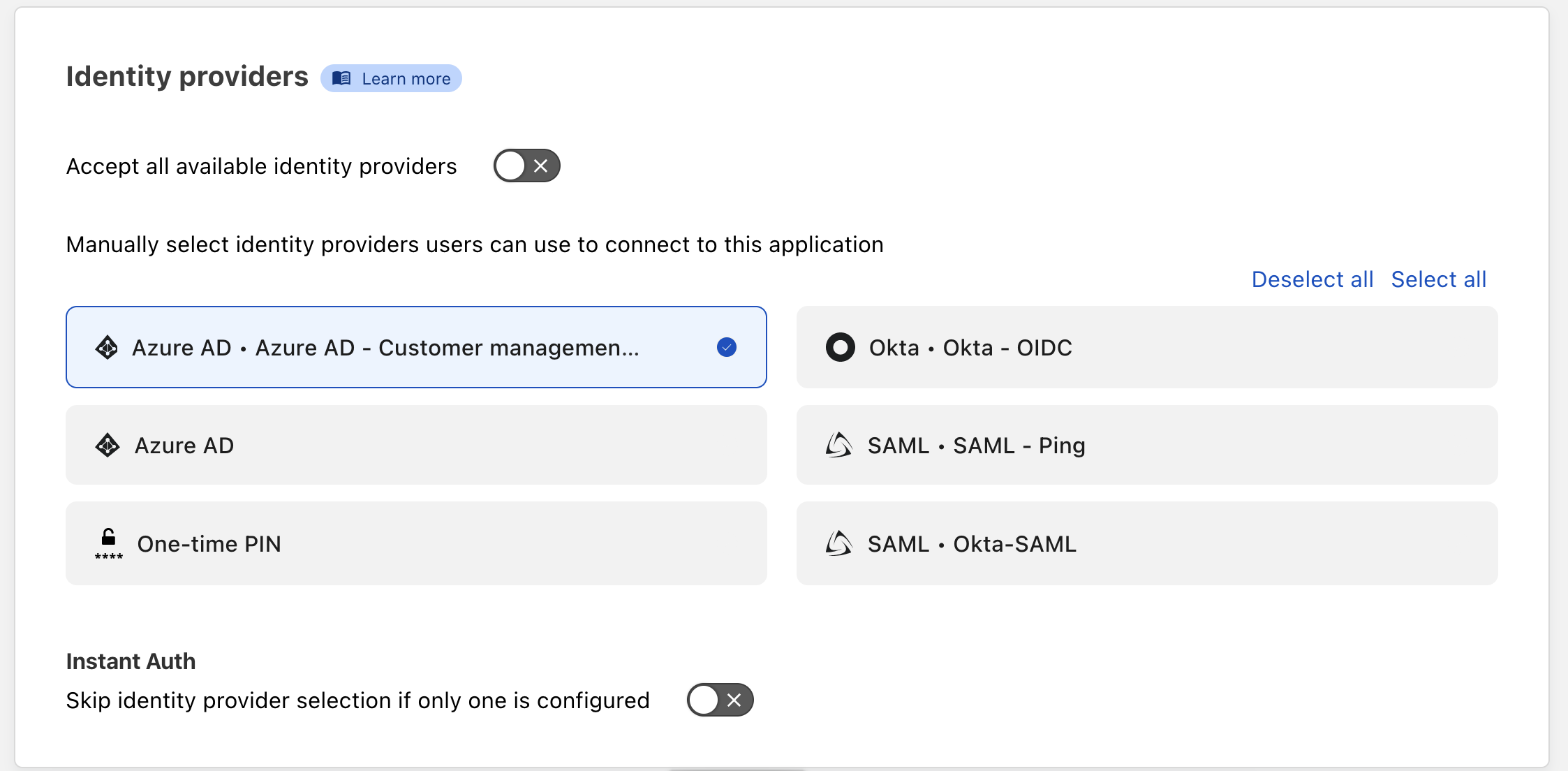
- Finally, create an Access policy to require logins from the selected IdP. For example:
Action Rule type Selector Value Allow Include Emails ending in @example.comRequire Login methods Azure AD • Azure AD - Customer management portal
Users will only be allowed access if they meet the criteria in your Azure AD Conditional Access policies.
You can reuse the same IdP integration for multiple applications as long as they require the same set of Conditional Access policies. For example, you could design a baseline IdP integration with a Conditional Access policy requiring MFA and a modern auth client. If an application requires special Conditional Access policies, you would need to set up a dedicated IdP instance for that application.