Configure DNS over TLS
By default, DNS is sent over a plaintext connection. DNS over TLS (DoT) is a standard for encrypting DNS queries to keep them secure and private. DoT uses the same security protocol, TLS, that HTTPS websites use to encrypt and authenticate communications.
Cloudflare supports DoT on standard port 853 and is compliant with RFC7858.
1. Obtain your DoT hostname
Each Gateway DNS location has a unique DoT hostname. DNS locations and corresponding DoT hostnames have policies associated with them.
- In Zero Trust, navigate to Gateway > DNS Locations.
- If you have more than one location set up, you will see a list of all your locations.
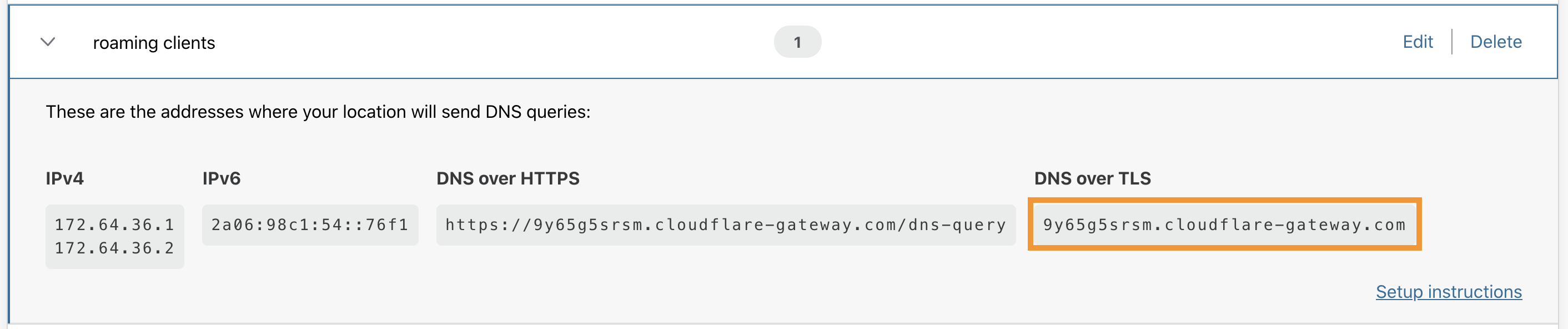
- Expand the location card for the location whose DoT hostname you’d like to retrieve.
- Get the DoT hostname for the location.
In the example below, the DoT hostname is: 9y65g5srsm.cloudflare-gateway.com.
Next, configure your DoT client with the DoT hostname.
2. Configure your DoT client
Depending on your operating system, you can choose from a variety of standalone DoT clients.
To configure your DoT client, enter the following IP address and the DoT hostname for your location (for example, 9y65g5srsm.cloudflare-gateway.com):
Hostname: <DoT hostname>IP address: 162.159.36.5Alternatively, stub resolvers (e.g., Unbound) support DoT natively. An example configuration is shown below.
# Unbound TLS Configtls-cert-bundle: "/etc/ssl/cert.pem"# Forwarding Configforward-zone: name: "." forward-tls-upstream: yes forward-addr: 172.64.36.1@853#9y65g5srsm.cloudflare-gateway.com forward-addr: <IPv6 address>#<DoT hostname> Supported TLS versions
Cloudflare’s DNS over TLS supports TLS 1.3 and TLS 1.2.